For my final project, my initial idea was to create a Twitter bot that would search an abstract feeling in Wikimedia Commons and post the first image that came up. The intent was to give an intangible feeling some kind of unrelated tangible picture.
Since I presented that idea, my project has changed a bit. I realized early on that I did not have the programming capabilities to achieve this, so I turned to If This Then That to aid me. That’s when I thought of using posts of things for sale on platforms like Craigslist and Ebay to outline these abstract feelings, making the posts even more abstract themselves.
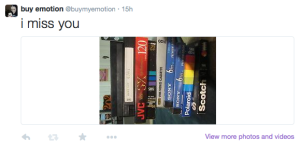
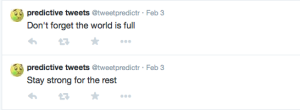
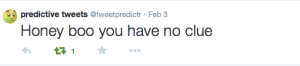
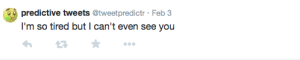
At first, I used IFTTT to create a trigger on Craigslist to tweet a photo when there was a post that said “Sad/Angry/Happy” etc. The post URL and any indication that the photo came from Craigslist was erased and replaced with only a cryptic tweet saying “I feel ___” corresponding with the feeling that triggered it.
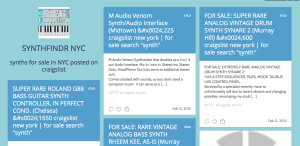
This proved to be difficult, as most of the posts on Craigslist that were triggering the tweets did not have photos. I decided to use Ebay instead since posts on Ebay always have photos and appear more often.
As for the triggering words themselves, I used obvious words in some cases like “anxiety” but for other feelings, I searched specific objects. Some examples are “recorded video tapes” for nostalgia, “crystal ball” for feeling lost (as they are stereotypically used to look into the future), and “donate” for needing help.
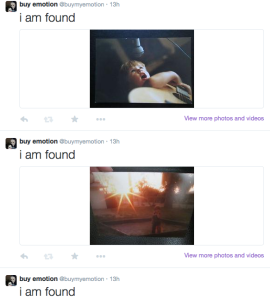
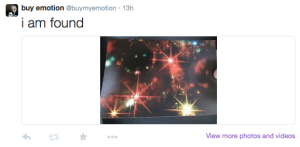
Some words like “found” were deactivated for a bit because they overtook the feed, as it was the most posted thing on Ebay. I want to continue experimenting with search terms and what the bot posts. The bot can be found here: https://twitter.com/buymyemotion